In the early days of computing, when the digital realm was still in its infancy, computers operated on a simple premise: they could execute a single program with full access to all the hardware resources on the machine. However, as technology rapidly advanced and computers grew increasingly powerful, a new paradigm emerged. Researchers and computer scientists began to realize that it made more sense to allow multiple programs to access system resources concurrently. This marked the birth of multitasking and the era of concurrent computing.
While the ability to run multiple programs simultaneously brought about significant benefits in terms of efficiency and productivity, it also introduced a profound challenge: security. In a world where multiple programs could potentially interact with system resources concurrently, the risk of malicious code wreaking havoc and compromising the integrity of computer systems became a pressing concern.
It was against this backdrop that cybersecurity experts and researchers embarked on a journey to devise strategies and technologies that would not only allow for the safe execution of multiple programs but also ensure the security and integrity of computer systems. Among the notable developments in this quest for heightened cybersecurity are the concepts of sandboxing, honeypots, and software containers.
In this comprehensive exploration, we delve into the world of cybersecurity and these three pivotal technologies, seeking to demystify their roles, advantages, and significance in safeguarding digital ecosystems. We’ll discuss the concepts, pros, and cons of each technology, and provide insights into when and how they are deployed to fortify our digital fortresses.
What Is Sandboxing?
Sandboxing is a term that encapsulates the idea of creating a controlled and isolated test environment within which to execute code. The concept draws its inspiration from a child’s sandbox, a small container where toys and sand are kept, providing a safe and confined space for children to play without making a mess elsewhere.
In the realm of software and computing, sandboxing involves the creation of an environment that restricts the actions of a program or code, ensuring that it operates within predefined boundaries. The primary objective is to prevent potentially harmful or untrusted code from adversely affecting the entire system or network.
The sandboxing approach serves a dual purpose. Firstly, it provides a secure space for developers to test new or experimental code, allowing them to observe its behavior and assess its impact without risking the integrity of the broader system. Secondly, it empowers security professionals to analyze older code for potential vulnerabilities by isolating the testing environment, enabling them to scrutinize the code thoroughly without compromising the underlying operating system or host devices.
Pros of Sandboxing:
- Testing Ground for Innovation: Sandboxing offers developers a safe environment to experiment with new ideas and code changes before they are deployed in production systems. This safeguards against the introduction of unstable or insecure code into the live environment.
- Vulnerability Analysis: Security experts can leverage sandboxes to scrutinize potentially harmful applications for vulnerabilities. By isolating the testing environment, analysts can confidently evaluate code without exposing the host system to potential threats.
- Risk Mitigation: Sandboxing limits the exposure of host devices to potential threats. Even if a piece of code behaves maliciously within the sandbox, it remains isolated and contained, preventing it from spreading to other parts of the system.
- Zero-Day Threat Detection: Sandboxing is a valuable tool for detecting zero-day threats, referring to previously unknown vulnerabilities that hackers exploit before developers have had a chance to patch them. By executing code in a controlled environment, sandboxes can detect and analyze suspicious behavior that might indicate a zero-day attack.
While sandboxing offers many advantages in terms of security and code testing, it’s important to note that it is not a panacea. Like any security measure, it has its limitations and may not be suitable for all scenarios. Furthermore, effective sandboxing requires meticulous configuration and monitoring to ensure its efficacy.
What Are Honeypots?
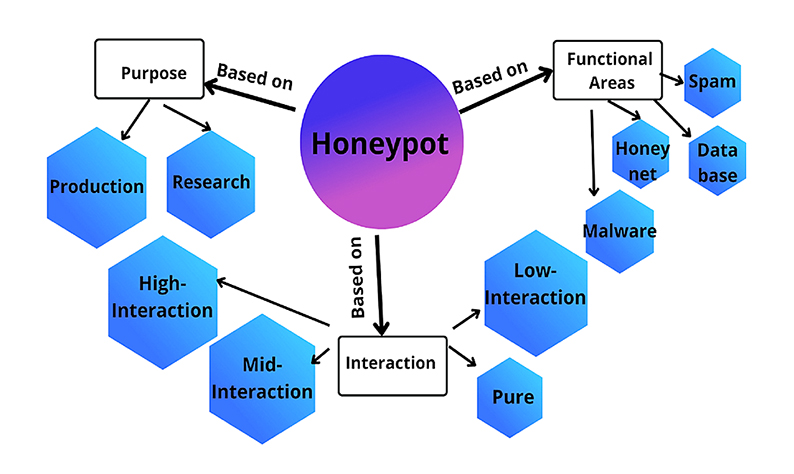
The term “honeypot” may evoke images of a sticky-sweet trap set to ensnare unsuspecting victims. In the world of cybersecurity, the concept is somewhat similar, albeit without the allure of sweetness. Honeypots are a cybersecurity tactic that focuses on deliberately creating systems or environments with known vulnerabilities to attract the attention of malicious actors—hackers.
The main objective of deploying honeypots is not to repel attackers with brute force but to collect accurate and valuable data about the attackers themselves. Unlike traditional security measures that aim to block or thwart intruders, honeypots take a more passive approach. They entice hackers by offering tempting targets—systems that appear vulnerable and enticing.
Here’s how honeypots typically work:
- Deployment: A company or organization sets up a few sensitive servers or systems and intentionally leaves vulnerabilities or “loose ends” untied. These vulnerabilities are designed to attract hackers.
- Lure and Observation: As hackers attempt to exploit these vulnerabilities and gain unauthorized access, the honeypots lure them into a controlled environment. This controlled environment can be a decoy network or a segregated part of the production network.
- Data Collection: While hackers interact with the honeypot, security researchers and professionals closely observe their activities. They gather valuable information such as IP addresses, ports being accessed, files being modified, and even the tactics and techniques employed by the attackers.
- Security Enhancements: The insights gathered from honeypots serve as a valuable resource for enhancing network security. Organizations can use this data to bolster their defenses, identify potential weak points, and devise strategies to counter similar attacks in the future.
Pros of Honeypots:
- Surveillance and Monitoring: Honeypots provide a means of spying on attackers and monitoring their movements within a controlled environment. This surveillance can yield critical intelligence about the tactics and techniques employed by malicious actors.
- Data Collection for Defense: The data collected from honeypots equips security teams with a wealth of information that can be used to improve network security. This data can lead to the development of new defense mechanisms and strategies to thwart future infiltrations.
- Insight into Zero-Day Attacks: Honeypots are particularly effective in gathering intelligence on zero-day attacks. As attackers attempt to exploit unknown vulnerabilities, honeypots capture their actions and behaviors, providing organizations with valuable insights into emerging threats.
- Early Warning System: Honeypots can serve as an early warning system, alerting security teams to potential breaches and attacks as they happen. This proactive approach allows for swift responses to mitigate damage.
While honeypots offer unique advantages in terms of threat intelligence and real-time monitoring, they also come with certain challenges. Deploying and managing honeypots requires expertise, and there is always a risk that attackers may detect and evade them. Additionally, the use of honeypots should be carefully considered within an organization’s overall cybersecurity strategy.
What Are Software Containers?
Software containerization is a relatively modern technology that has gained immense popularity in the realm of cybersecurity and software development. Major tech giants, including Microsoft, Google, and Facebook, have embraced containerization as a means to create isolated user-space environments for their applications.
At its core, containerization revolves around the concept of bundling all the components of an application into a single, self-sufficient unit known as a container image. This container image encapsulates everything the application needs to run, including binaries, libraries, dependencies, and configuration files.
What sets containers apart is their ability to run in isolation on the same underlying operating system, sharing resources with other containers. This isolation is achieved through the use of container runtimes, such as Docker, which ensures that each container operates independently.
The key features and benefits of software containers include:
- Lightweight: Containers are exceptionally lightweight because they only contain the essential components and dependencies required for an application to run. This efficiency allows for rapid deployment and scaling.
- Compatibility: Containers address platform compatibility issues by bundling all the necessary components within the container image. This means that an application encapsulated in a container will run consistently regardless of the host environment.
- Portability: Containers can be easily deployed across various environments, including development, testing, and production. This portability streamlines the process of building, shipping, and running applications, promoting consistency and reliability.
- Resource Isolation: Containers operate within their isolated environments, preventing interference with other containers or the host system. This resource isolation ensures that a problem or malfunction within one container does not affect others, enhancing system stability.
The advantages of containerization have made it a favorite choice for developers and system administrators alike. It simplifies the process of managing and deploying applications, reduces overhead, and promotes consistency in application behavior across different environments.
Using Sandboxes, Honeypots, and Containers in Cybersecurity
Now that we’ve explored the concepts and advantages of sandboxing, honeypots, and software containers individually, it’s crucial to understand how these technologies are deployed within the realm of cybersecurity.
Sandboxing is a valuable tool when there is a need to analyze potentially harmful applications or code changes before they are introduced into a production environment. It provides a safe space for developers to test new features or modifications without risking the integrity of the live system. Additionally, sandboxing plays a pivotal role in the detection of zero-day threats—previously unknown vulnerabilities and exploits. By executing code in a controlled environment, sandboxes can identify suspicious behavior and potential security risks.
Honeypots, on the other hand, are primarily deployed with the aim of surveillance and data collection. Organizations that want to gain insights into the tactics, techniques, and procedures employed by attackers often employ honeypots. By deliberately exposing enticing but controlled targets, they lure hackers into an environment where their actions can be closely monitored. The data collected from honeypots serves as a valuable resource for improving network security and developing strategies to counter similar attacks in the future.
Software containers have revolutionized the way applications are developed, deployed, and managed. While their primary purpose is not security per se, they offer inherent security benefits. Containers ensure that applications run consistently across different environments, reducing the risk of compatibility issues and promoting a secure development and deployment pipeline. The isolation provided by containers also enhances security by preventing one container from interfering with others on the same host system.
The choice of which technology to employ in a given cybersecurity scenario depends on the specific objectives and requirements of the organization. Here are some considerations to guide the decision-making process:
- Sandboxing is an excellent choice when there is a need to analyze potentially harmful applications, test code changes, or detect zero-day threats. It offers a secure testing environment and helps in identifying and mitigating security risks before they impact the production environment.
- Honeypots are deployed when the focus is on observing and tracking attackers’ movements within a controlled environment. Organizations that wish to gather valuable intelligence about adversaries and enhance their defense strategies find honeypots to be a valuable asset.
- Software containers are ideal for organizations seeking to streamline the deployment and management of applications while maintaining a consistent and secure development and deployment process. Containers enhance application isolation and resource management, contributing to overall system security.
In summary, the choice of whether to employ sandboxes, honeypots, or containers—or a combination thereof—depends on the specific security goals and challenges faced by an organization. Each of these technologies serves a unique purpose within the cybersecurity landscape, and understanding their strengths and limitations is crucial for building robust defense mechanisms.
Conclusion
The evolution of cybersecurity has been closely intertwined with the development of innovative technologies and strategies designed to protect digital ecosystems from evolving threats. Sandboxing, honeypots, and software containers represent three distinct but interconnected pillars of cybersecurity, each with its unique strengths and capabilities.
Sandboxing provides a secure testing ground for developers and analysts to assess code changes and detect potential threats before they reach the production environment. It is a valuable tool for safeguarding against zero-day attacks and vulnerabilities.
Honeypots take a more passive approach, deliberately enticing attackers into a controlled environment. By observing and collecting data on hackers’ activities, honeypots empower organizations to enhance their security measures and gain valuable insights into emerging threats.
Software containers have redefined the way applications are developed and deployed, offering both efficiency and inherent security benefits. Containers promote consistency and isolation, ensuring that applications run reliably across different environments.
In the ever-evolving landscape of cybersecurity, organizations must carefully consider their unique security requirements and objectives. The deployment of sandboxes, honeypots, or containers—or a strategic combination of these technologies—can significantly enhance an organization’s ability to defend against cyber threats and adapt to the ever-changing digital landscape. As the cybersecurity field continues to evolve, so too will the tools and strategies at our disposal, shaping a more resilient and secure digital future.