In the realm of software development, Google’s Chrome is a heavyweight, and the language behind its success, C++, is now undergoing a transformation aimed at improving memory safety. The goal is to reduce memory-related security flaws, such as buffer overflows and use-after-free vulnerabilities, that are prevalent in the C++ codebase of Chrome.
While Rust, with its robust memory safety guarantees, has gained popularity in recent years, transitioning Chrome’s extensive codebase to Rust is not a feasible short-term solution. Instead, Google’s Chrome team is exploring innovative methods to make C++ safer for developers while maintaining its high performance.
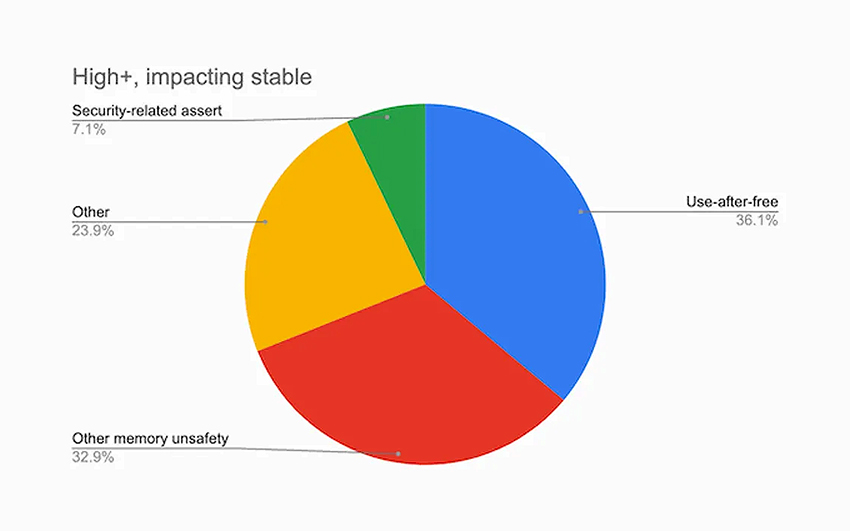
C++ lacks inherent memory safety, which often leads to vulnerabilities arising from dangling pointers and the reuse of memory still reachable. Dangling pointers occur when memory used by an application is returned to the system, but pointers continue to reference outdated objects, ultimately leading to use-after-free issues that can be challenging to identify in large codebases.
To combat these vulnerabilities, Google has implemented various strategies, including C++ smart pointers, static analysis in compilers, code sanitizers, code fuzzers, and a garbage collector called Oilpan. Rust, however, stands out because its compiler detects pointer mistakes before code execution, preventing such issues without incurring significant performance penalties.
A promising avenue that Google is exploring is heap scanning, designed to prevent the reuse of memory until it is verified that no dangling pointers reference it. This approach uses quarantines and heap scanning to enhance memory safety without altering C++ code or semantics.
Here’s how it works: When memory is deallocated (via delete), it enters a quarantine, becoming unavailable for reuse by subsequent allocations. Periodically, a heap scan is triggered, much like a garbage collector, to identify references to quarantined memory blocks. Blocks with no incoming references from the regular application memory are then made available for reuse.
While heap scanning shows promise, it comes with a performance cost, particularly in C++ applications. Google’s Chrome team experimented with hardware-assisted memory tagging via ARM v8.5A’s memory tagging extension (MTE) to address this issue. The results were encouraging, with MTE helping to reduce the performance overhead associated with heap scanning.
This approach could offer a path to improved memory safety in C++, all while maintaining high performance. However, it is currently dependent on the widespread adoption of hardware memory tagging, which remains a work in progress.
In conclusion, Google’s efforts to enhance memory safety in its Chrome browser exemplify its commitment to both performance and security. The exploration of heap scanning, combined with hardware memory tagging, could pave the way for a safer C++ experience in the future, benefiting developers and users alike. As technology evolves, we can anticipate further refinements and optimizations in this endeavor to bolster the security of C++ applications.